Quickly Dealing with Website Spam Bots
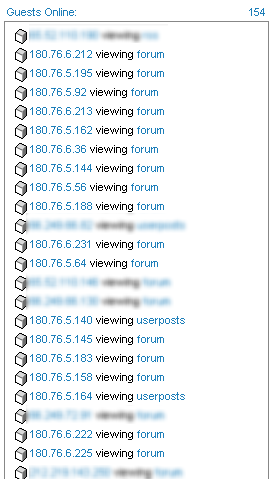 If you look in the image to the right, one of the community based sites I’m involved with was seeing a higher than normal user count for this time of the morning, which probably meant that it was being attacked by users or most likely spam bots.
If you look in the image to the right, one of the community based sites I’m involved with was seeing a higher than normal user count for this time of the morning, which probably meant that it was being attacked by users or most likely spam bots.
Looking through the IP addresses, there was a common theme the IP ranges 180.76.6.* and 180.76.5.* which are located in China (we have no users in China see here for a lookup tool)
Now that’s pretty easy to crudely solve using a .htaccess file, regex and apache rerewrite rules.
Because I want to cover two subnets, I’ve written two rules, they are simply:
#180.76.6.* and .5
RewriteCond %{REMOTE_ADDR} ^180\.76\.5\.
RewriteRule .* http://www.google.com [R,L]RewriteCond %{REMOTE_ADDR} ^180\.76\.6\.
RewriteRule .* http://www.google.com [R,L]
If you desired to just block a single address then you would need a slightly different rule, which would be:
RewriteCond %{REMOTE_ADDR} ^180\.76\.6\.183$
RewriteRule .* http://www.google.com [R,L]
This won’t stop their current connection, but as soon as the user agent goes to reload or navigate to another page, then in this example they’ll be sent to google.com instead (although I can assure you they are not being redirected to google in the live example of this).
Coping with a siege such as this example speed is of the essence and this is a quick and dirty way of dealing with them and also highly amusing as you chose where they are redirected to (but for goodness sake, make sure you check this works with your IP or IP range first!)
Ideally configuring a firewall wall before they even hit the site would be more suitable along with a few other methods of identifying them without being altered to the attack in the first place.